The two types of monitoring which Keyfactor Command offers for certificate authorities are configured on the Alert Recipients tab of the Certificate Authorities page at Locations > Certificate Authorities. Monitoring is not supported for CAs accessed with the Keyfactor Universal Orchestrator![]() The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers..
The Keyfactor Universal Orchestrator, one of Keyfactor's suite of orchestrators, is used to interact with servers and devices for certificate management, run SSL discovery and management tasks, and manage synchronization of certificate authorities in remote forests. With the addition of custom extensions, it can provide certificate management capabilities on a variety of platforms and devices (e.g. Amazon Web Services (AWS) resources, Citrix\NetScaler devices, F5 devices, IIS stores, JKS keystores, PEM stores, and PKCS#12 stores) and execute tasks outside the standard list of certificate management functions. It runs on either Windows or Linux servers or Linux containers..
 Certificate Authority Health Monitoring
Certificate Authority Health Monitoring
Enable certificate authority![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. health monitoring to receive email alerts when one or more of your CAs is not responding. Only CAs configured for synchronization will be monitored for health. To enable health monitoring, configure one or more recipients to receive the email messages and configure a health check schedule. You can choose to schedule the health checks either for daily at a specified time or at intervals of anywhere from every one minute to every 12 hours.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. health monitoring to receive email alerts when one or more of your CAs is not responding. Only CAs configured for synchronization will be monitored for health. To enable health monitoring, configure one or more recipients to receive the email messages and configure a health check schedule. You can choose to schedule the health checks either for daily at a specified time or at intervals of anywhere from every one minute to every 12 hours.
 Certificate Authority Threshold Alerts
Certificate Authority Threshold Alerts
Enable threshold alerting to receive email alerts when a CA![]() A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. issues more or fewer certificates or experiences more failures or denials than configured for monitoring on the CA. Setting threshold monitoring is a two-step process:
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. issues more or fewer certificates or experiences more failures or denials than configured for monitoring on the CA. Setting threshold monitoring is a two-step process:
- Configure monitoring on the advanced tab (see Advanced Tab) for each CA.
- Set the email recipients for the alerts on the alert recipients tab of the certificate authorities page.
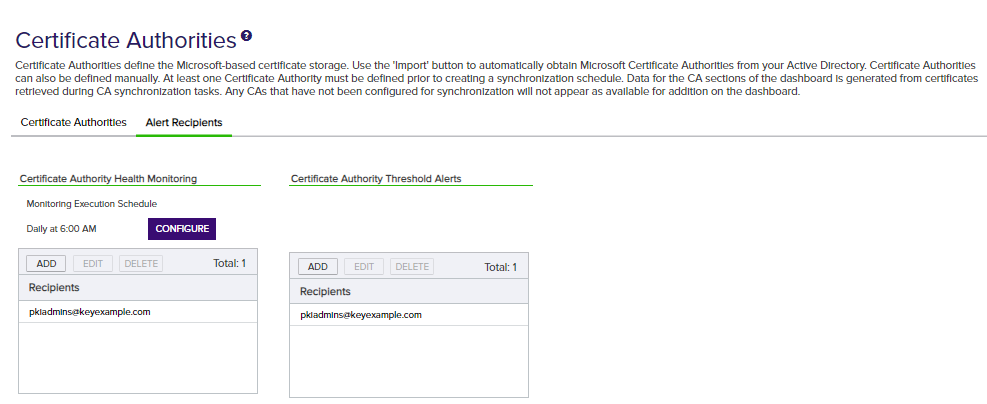
Figure 222: Certificate Authority Monitoring Recipients